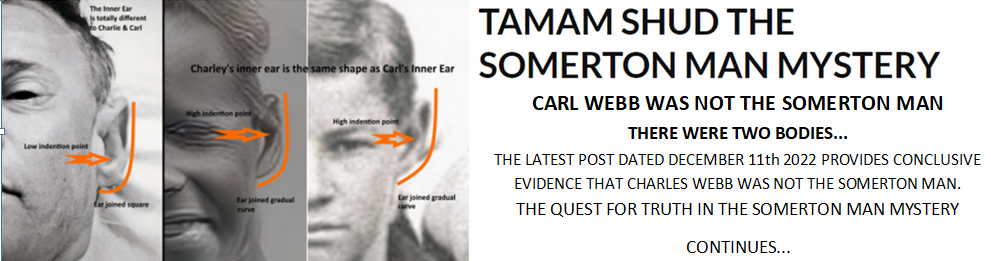
What constitutes a ‘Legend’ ?
Let’s start with the Oxford dictionary definition:
A traditional story is sometimes regarded as historically correct but not authenticated or substantiated. As in “The Legend of King Arthur".
Similarly, we often refer to sporting heroes as ‘legends’ or append it to the names of the famous and describe their exploits, good or dubious, as 'legendary'. But the ‘legend’ that we could append to the “SOMERTON MAN’ has an entirely different meaning
I say ‘could append’ because there is no certainty about the accuracy of what I am about to describe. It based on what I have learned about the world's second-oldest profession, the science, art and practice of espionage
In the world of spies and espionage, the term LEGEND refers to the story that a field agent may 'wrap' around his real identity, his biography in a way.
Here's an outline, by no means complete of what you might expect in a spy 'Legend'
1. History.
To commence the legend, the spy must have a convincing story about his or her past, their date and place of birth, and names of parents, siblings and relatives. People they knew at school or had worked with. Details about the town where they grew up, employment history. And all of this and more would be accompanied by the relative documents, fake of course. People who were employed to provide these documents were known as 'shoemakers'. One such person was Jacob Golos, a soviet spy who left this world in 1943 due to a heart attack, or so it is said. Read more here:
2. Possessions. Planning to the minutest detail is required in the building of a legend. For example, a man who was had as his 'cover' the identity of an itinerant worker who took on basic work be it on a cattle station or in a printer's workshop would have all the trappings that would be expected of such a man. His clothes may be neat and tidy but with one or two repairs, his shoes would be clean, and his pockets would have a range of normal everyday items, cigarettes, matches, a comb, and some chewing gum. You could even throw in a few travel tickets, or random items. Everything would appear to be as normal as possible. When it came to his clothes though, he might want to remove the labels and anything that would identify him or where he had been on his travels, spies were known to do this if they knew they were heading into a dangerous situation.
The deception would even extend to a suitcase deposited at a railway station, it too would be filled with nothing extraordinary, some hand-crafted bits and pieces and clothing.
Collectively, the items on his person and the suitcase contents are known as 'litter', put there to allay suspicion if caught. It was all part of the 'legend'.
By now of course you will have seen that all of these things could apply to the Somerton Man. A very ordinary working man who, apparently ended his life on a beach at Somerton in South Australia.
But, and it's a big but, two mistakes were made. Mistake 1 was the fact that the left luggage ticket was missing, nowhere to be found and 2, and perhaps the most telling of all, was a tiny scrap of paper with the words TAMAM SHUD typeset on to it, rolled up tightly and pushed well down into a concealed, secret, waistband fob pocket of the trousers the man was wearing when his body and clothing were subsequently examined. Why would he have done that? What was so special about that scrap of paper that it had to be concealed in the way that it was? The answer as per previous posts, is that on that tiny scrap of paper was some information, so valuable that he was killed for it.
The man died and the presence of a 'legend;, is a strong possibility but not, as yet, a probability. Dead spies tell no stories. and the legend is no more. Until that is, we completely crack the codes that were found and associated with him.